top of page


Unleashing the Power of Docker: Streamlining Containerization for Modern Development
Explore Docker's role in transforming containerization, enabling scalable and efficient software development processes.

Bhavin Bhesaniya
Jan 26, 20254 min read

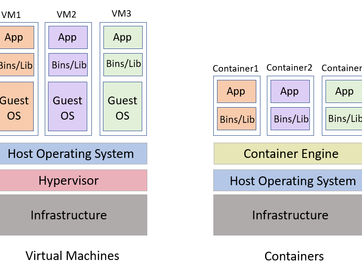
Exploring Containerization vs. Virtualization: Which is Right for Your Workload?
Learn the differences between containerization and virtualization to choose the right solution for your workload and infrastructure needs.

Bhavin Bhesaniya
Jan 26, 20252 min read


Essential DevSecOps Tools to Strengthen Security and Streamline Processes
Explore the 10 must-have DevSecOps tools to improve security and streamline your development and deployment processes.

Bhavin Bhesaniya
Jan 26, 20255 min read


CI/CD Pipelines Uncovered: A Complete Guide from Code to Deployment
Explore CI/CD pipelines and learn how to automate the journey from code to deployment for efficient software delivery.

Bhavin Bhesaniya
Jan 26, 20255 min read


Comprehensive Guide to Security Testing in DevSecOps: SAST, DAST, IAST, SCA, and RASP
Learn about SAST, DAST, IAST, SCA, and RASP in DevSecOps for a secure software development process.

Bhavin Bhesaniya
Jan 26, 202511 min read

Demystifying DevSecOps: An Inside Look at the Lifecycle of Secure Development Operations
Explore the lifecycle of DevSecOps and discover how to build secure and efficient development operations.

Bhavin Bhesaniya
Jan 26, 20255 min read


DevSecOps Demystified: Building a Secure Software Development Framework
Discover essential DevSecOps strategies for building secure and efficient software development processes.

Bhavin Bhesaniya
Jan 26, 20255 min read


Uncovering IDOR Vulnerabilities: A Comprehensive Guide
IDOR (Insecure Direct Object Reference) lets attackers access unauthorized data by tampering with object references in requests.

Bhavin Bhesaniya
Oct 4, 20244 min read


Maximizing Security with OpenVAS: A Comprehensive Guide to Vulnerability Assessment and Management
OpenVAS is an open-source vulnerability scanner that helps identify security weaknesses, enhancing your organization's cybersecurity posture

Bhavin Bhesaniya
Oct 4, 20245 min read


Uncovering the Threat of SQL Injection: Understanding the Different Types, Exploits, and Effective Defenses
Uncovering the Threat of SQL Injection: Understanding the Different Types, Exploits, and Effective Defenses

Bhavin Bhesaniya
Oct 4, 20245 min read
bottom of page
